Almost all the machines out of the stores in the past two years, whether laptop or desktop, are connected to the worldwide web, which makes them target of malicious activities.
Another problem is that the common good protection applications fail to detect 100% of the invaders knocking on the door of the user.
A common type of spyware is one which intends to steal data, but to use the computer as a zombie,using your internet connection to hack sites and services available on the network. There is a way to monitor your internet connection and see all and any website or IP address that is accessed through your router.
How to find hidden Process activities?
The first step to discover what services are being accessed on your computer is to start the Windows command prompt with administrator privileges. For this, open the Start menu and type “cmd” in the search space. Then, click the right mouse button on the Match and choose the item “Run as administrator”.
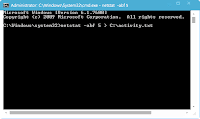
Use the command “netstat” to record all activities that access the Internet in some way. For this, just type in the instruction as shown below:
netstat-abf 5 > PATH/activity.txt“PATH” must be the directory where the file “activity.txt” will be saved. It can be any folder on your computer.
The letter “-a” command means that all connections and gates shall be heard and stored in the file, the “-b” shows which applications are creating ways to access the internet, the “-f” will record the full DNS each connection, to facilitate understanding of the data. If you want only the IP addresses are recorded, put the “-n” in place of “-f” make it “-abn”. The value “5″ indicates the length of time, in seconds, from one reading to another.
Nothing will be displayed on the screen while the command is being executed. After a few minutes, press Ctrl + C to finish the reading of the connections and stop recording data in the file. Now we just have to open the text file created and begin to analyze what services were accessed from your computer.
How to interpret results
When you open the file activity.txt, you will notice that the content is divided into four main columns:
Protocol: states the type of protocol used to access.
Local and Foreign Address are IP addresses.
State column shows the activity that was being made at the time of reading.
It is in the third column where all efforts will be concentrated, as this indicates the external IP addresses and URLs accessed by your machine. An easy way to find suspicious activity is to look at the name of the processes presented in brackets throughout the document.
Noticed something different, check the Foreign address you use. If you still can not identify what it is, a good start is to look for the name of the activity on Google. If common in computers, surely there somewhere that explains what it is.
Another way to discover the service is accessed using a service that tracks IP addresses. Two good choices are IP Address Tracer and Global Whois Search. In both cases, you only need to copy the IP in the search space and wait until the search is completed and the data begin to appear on the screen.
Other tools
There are several applications that help monitor the doors and open connections on a computer.CurrPorts is one of the most used by users with a little more experience, it is relatively easy to use and interpretation of results displayed on the screen gives more natural.
Wireshark is also more suited to who owns a home computer network, as this also examines the exchange of messages between machines connected by the hub (or switch). Thus, if a computer is infected and the invasion propagates through the network, manages to detect without major problems.
What do I do next?
If the test result says that the process is, in fact, an invader, it is necessary to take some steps to be removed from the computer and not use more than your connection. The simplest way to do this is to use security applications such as anti-spyware, that analyze the machine for possible internet virus.
If the tools have no effect on the potential invader, one option is to search the World Wide Web specific to certain virus injections. Google always helps. It is very common for security companies to launch free solutions to fix only certain threats. If still you are finding it difficult and unsure then get a tool calledSpyware Doctor Full version for just 18.99$ to be on safe side and let it handle all dirty work.
Now that you know how to use “netstat” and saw how easy it is to interpret the data and use the information provided, it begins to scan your computer to find out if there are any hidden process running and if your connection is hurting. Then again do not forget to leave us a comment telling your experience.
There are several programs that help to protect your machine from these spywares, but not always sufficient to prevent them from invading your computer.

No comments:
Post a Comment